In Beyond Passwords: Stronger Authentication, Part 1, we explained the problem and showed why organizations are interested in improving on password authentication. In part two, we examine the solution.
Organizations that want to implement stronger authentication have a dizzying array of alternatives and products to choose from. To get started, let’s break the alternatives down into categories and identify a few products in each category.
Digital Certificates
Digital certificates are based on Public
Keys, a cryptographic system whereby pairs of keys are generated with a unique mathematical property: anything encrypted by one key can only be decrypted by the other key. In each pair, one key must be safeguarded and known only to the legitimate user — this is the Private Key. The other key is given freely to everyone who wants to authenticate the private key holder — this is the Public Key. If you encrypt a known value with your Private Key, anyone else can decrypt that value with your Public Key and compare those two values. If they match, you are considered authentic because you demonstrated that you hold the Private Key.
For authentication, your identity must be somehow tied to your key pair. This is the purpose of Digital Certificates. A certificate binds a public key to a named entity and some information about that entity (like company, state and country). Although this binding could be supplied to each correspondent out-of-band, that would not scale well or let strangers authenticate each other. To solve this, certificates are issued by Certificate
Authorities (CAs): trusted third parties that generate and “sign” certificates using their own private keys. In this way, everyone can know the public keys of a few trusted “root” CAs and accept any certificates generated by those CAs.
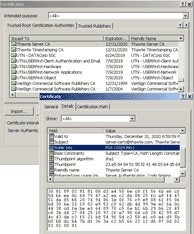
Digital certificates form the basis for the SSL server authentication widely used by e-commerce sites. Every Web browser includes a list of well-known root CAs. For example, Internet Explorer’s trusted root list includes Thawte‘s certificate (below).
2. One-Time Passwords
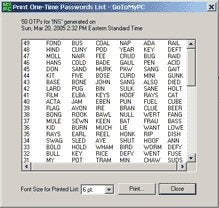
Let’s jump to the opposite end of the complexity (and security) spectrum to consider One Time Passwords (OTPs). Password crackers rely on people reusing the same password. Cracking a password that’s only good for a single use is of little practical value. OTPs capitalize create an authentication system whereby each password can be presented for authentication just once. After an OTP is used, it can never by used again (or at least not any time soon).
OTP authentication systems rely upon a pre-defined relationship and synchronization between the user and authentication server. A well-known, freely available OTP system is S/KEY, developed by Bellcore in the ’90s as the basis for RFC 2289, the IETF OTP standard. The user provides a secret and a number of passwords to generate, and the password generator creates an ordered list of passwords. When the user tries to authenticate, the OTP is sent to the server. If authentic, the server adjusts the user’s password counter so that, next time, he’ll be prompted for the next OTP on the list and so on.
S/KEY utilities are freely available for virtually every operating system, including:
3.Hardware Tokens
Hardware tokens are the most popular two-factor authentication method in use today. Traditional tokens take the concept behind one-time password generation to a whole new level, combining that with a second authentication factor. Newer hardware tokens tend to pair different kinds of credentials, skipping passwords altogether.

(right) illustrates a traditional RSA Security SecurID Fob and SecurID
PINpad. As we can see, both tokens display a number — this is effectively a one-time password. However, instead of being statically generated with an algorithm like S/KEY, a new pseudo-random number is dynamically-generated every
60 seconds. The next number cannot be predicted or guessed, except by the Authentication Server that initialized the token.
After initialization, whenever the user attempts to authenticate, she is prompted for a “passcode.” In response, she types the number currently displayed on the token, followed by her Personal Identification Number (PIN). This interaction is similar to “normal” password authentication, so it fits well with many protocols and applications. If the user reaches the end of a 60-second interval, she may be prompted for another passcode, and of course she cannot authenticate if she’s accidentally left her token at home. Replacing a lost token isn’t as instantaneous as resetting a forgotten password. However, many organizations consider these to be minor inconveniences in light of the significantly stronger authentication that two-factor hardware tokens offer.

(non-interactive) forms of strong authentication. For example, the Verisign
Unified USB Authenticators illustrated at right are available in two form factors — one that supports token code display and another that does not.
USB hardware token functions vary quite a bit, but generally support more automation and multiple authentication methods, including digital certificates.
For example, ActivCard‘s USB Key stores a user’s private keys, passwords and profiles for network access. You plug the key into a USB port on your computer and enters histour PIN. Thereafter, you can be authenticated using any of the credentials stored on the key — legacy password, dynamic one-time password or certificate. USB keys work with client software installed on the user’s computer—in this example, ActivCard Gold.
Many vendors sell authentication tokens. Most sell an assortment of hardware, including fobs and USB keys and combinations thereof.
Some also sell passcode-generator software to turn a small-footprint device like a PDA or Smartphone into a token. A few examples of vendors in the hardware token market include:
Allocating tokens, replacing damaged or lost tokens, and purchasing the associated authentication server software does involve cost. For example, a 2004 Infrastructure Software and Systems Management survey published by the Susquehanna Financial Group stated that RSA Security’s average selling price is about $40 per token with a typical three-to-four year life.
Vendors do compete vigorously on token pricing and offer volume discounts, so consider this merely as one example, and do your own shopping.
4. Smart Cards
With the advent of USB tokens, the division between Smart Cards and tokens has become somewhat fuzzy. But traditional Smart Cards are what you no doubt picture — a plastic card, the same size as most credit cards, with an electronic microchip embedded right into the card. The chip contains information about the cardholder that can be read only by a card reader. Although Smart Cards have many possible uses — for example, as a pseudo-cash card to make point-of-sale payments, or as a badge to enter a secure facility — they can also be used for network authentication. In particular, the microchip can store the cardholder’s digital certificate and key pair.
For example, below we show the VASCO Digipass Go2, a card reader that accepts various compatible Smart Cards. Note that some bank credit cards issued today are, in fact, Smart Cards. To use this device, you insert your card and enter a PIN into the reader. Thereafter, you can respond to Digipass Authentication Server prompts until the card is removed from the reader.
Smart Card readers don’t have to be standalone devices. The ActivCard PCMCIA Reader (below) is capable of reading the information embedded in the microchip on the adjacent ActivCard Corporate Access Smart Card. If you can insert your Smart Card into a PCMCIA slot, why not use a USB port? And that is, in fact, what many USB Keys are: Smart Cards in a USB form factor.
Form factor matters quite a bit to end users, so you’ll want to choose carefully when deciding what kind(s) of hardware credentials to issue with a premium authentication service. Consider where and how your employees work, devices they carry and credential portability (for example, do they need to authenticate from a public PC). From a security perspective, carefully consider which factors any given Smart Card supports, the security of the token/card/reader and associated client/server software, and compatibility with the network services and applications to be accessed.
5. Biometrics
Certificates, OTPs, tokens and smart cards all represent “something you have.” Let’s briefly consider that third authentication factor: “something you are.” Authentication methods that employ this factor are known as biometrics. Biometric authentication samples physical characteristics and uses them to verify the user’s claimed identity.
Perhaps the most well known biometric method is fingerprint analysis.
Fingerprint authentication captures an image of the user’s fingerprint, identifies unique points and patterns and compares them to a biometric template created during an earlier (and known valid) scan of the user’s fingerprint.

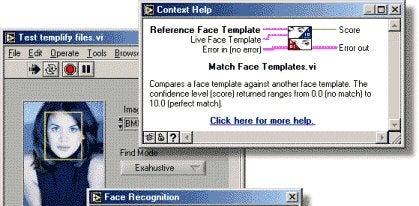
Facial recognition is another well-understood biometric method. For example, the VISecurity BiometricsVIEW toolkit illustrated below translates a facial image into numerical samples that can be used on subsequent scans to authenticate that person. Facial recognition products must overcome differences that change a person’s appearance, such as lighting, haircut, glasses and aging.
Handwriting (signature) analysis can also be used for biometric authentication. If you’ve watched CourtTV, you know that each person’s handwriting is unique. Analysis may take into account the shape and appearance of a person’s signature; parameters like pressure and timing can also be measured when a person signs their name. For example, CIC SignatureOne server and Sign-it client software enable real-time signature capture and verification. Handwritten signature programs like Cryptosign can be used to unlock PDAs, making it harder to steal or use any credentials that might be stored there.
Authentication through iris scanning is possible because every iris (the colored ring around the pupil of your eye) has a unique pattern that forms during a person’s first year and remains the same thereafter. Iris patterns have unique characteristics that can be scanned from a few feet away with a high-resolution camera. Like fingerprints, iris images can be mapped and stored as biometric profiles for future comparison during authentication. Iris scanning is considered highly reliable, with few false positives, although a bit more expensive than some other biometric methods. For example, see Iridian‘s KnoWho Authentication Server.
Retina scanning is conceptually similar to iris scanning, but analyzes patterns made by blood vessels in the back of the eye. Like iris scanning, retina scanning uses cameras and is highly accurate, but it requires close proximity to the eye and is thus more intrusive.
In comparison, voiceprint recognition is inexpensive and non-intrusive. Voice samples can be easily recorded and compared, evaluating characteristics like tone, pitch and cadence. On the other hand, a person’s voice changes throughout their lifetime, including temporary changes due to illness, hoarseness, etc.. Environmental factors like background noise and distance from microphone readily affect voice samples. For example, see Nuance Verifier, a voice authentication platform used to secure telephone transactions through a combination of voice recognition and PINs. A system like this could be used to add strong authentication to a change request process.
These are just a few of the many biometric authentication methods and products now available. Of these, fingerprint recognition is probably the most commonly deployed method in business networks. However, biometrics in general trail the use of other authentication methods covered in this primer, largely due to deployment costs. Today, biometrics are more likely to be employed in high-risk scenarios, but if costs drop, they may someday be preferred to other authentication methods. To learn more about biometric authentication and vendors in this field, visit the Biometric Consortium or the International Biometric Industry Association (IBIA) Website.
Conclusion
Ultimately, deciding when and how to implement or upgrade your company’s authentication infrastructure requires careful consideration of your business needs and the associated costs and benefits. We hope this primer has given you food for thought about why there’s a need for better-than-password authentication and places to learn more about strong authentication products and services.
Adapted from ECommerce-Guide.com, part of Internet.com’s Small Business Channel.
| Do you have a comment or question about this article or other small business topics in general? Speak out in the SmallBusinessComputing.com Forums. Join the discussion today! |