Web developer Dave Smith wasn’t entirely surprised when one of his clients, a small clothing e-tailer in southern California, came to him recently and said the site Smith developed for him had been hacked.
Smith is not his real name, and he won’t tell us his client’s name — even off the record. “It would just be so damaging for him if this came out,” he says.
Hacking is the dirty little secret of the e-commerce world. It has become a major risk factor for Web merchants, especially under-resourced small businesses. Hackers can break in to servers through Web applications and steal customer credit card information, or worse.
Developers, like Smith, who cater to small merchants know about many of the vulnerabilities and make sure they protect their clients, but they can’t know about all of them, especially if they use off-the-shelf components, as Smith did. It was the shopping cart software he used that turned out to be the weak link at this particular site.
As in most such cases, the site owner found out about the vulnerability only when an angry customer called to say that someone had used his credit card illegally — and that this was the only site at which he’d bought anything with it himself.
When Smith investigated, he found that the version of the shopping cart software used at the site did in fact have known hacker vulnerabilities. They had been fixed in a subsequent upgrade, and the software company had also posted coding changes that site developers could implement to remove vulnerabilities in older versions.
But a few weeks after Smith made the recommended changes, his client reported more angry customers claiming their credit card information had been recently stolen. “That was enough for us to bring down the site,” Smith says.
It Could Happen to You
The impact of the hacking was considerable. His client had lost the trust of several valued customers. Voluntarily shutting down the site resulted in further loss of revenue. And the only solution was either an extensive overhaul of the site using different software — dismissed as far too expensive — or a full upgrade to the latest version of the existing shopping cart software. Even the less expensive option ended up costing “a few thousand” dollars, Smith says.
“But my client said to me, ‘How do we even know this upgrade will fix the problem?'” he recalls “You know, I don’t know how to answer that. The problem is just so subtle.”
|
|
Seal of Approval — ScanAlert’s Hacker Safe logo certifies that an e-tailer has taken steps to protect the site — and customers — from hackers. |
That’s when he went looking for a solution and found ScanAlert Inc., a Web security auditing and monitoring firm that certifies sites “Hacker Safe” and allows them to display a certification mark similar to companies — such as TRUSTe’s — that certify sites as having acceptable privacy policies.
He rebuilt the site using the upgraded shopping cart software. ScanAlert used its automatically scanned both the new site before it went live and the old one that was still using the patched older version of the cart software. The new one showed no vulnerabilities, the old one remained hacker unsafe.
Smith’s client is one of the relatively lucky hacking victims, says ScanAlert director of customer support Scott Shebby.
“Eventually, credit card companies get wind of the fact that a site has vulnerabilities,” Shebby says. “They have ways to track it back. And when they do, they make sure you’re shut down and that you can only get back up again on their terms.”
That could mean being out of business on the Web for a month — disastrous for Web-only merchants — and technology fixes that could cost $20,000 or more. This is just one reason it makes sense to use the ScanAlert service, Shebby argues. At as little as $179 a month (with a one-year contract), ScanAlert prevention costs less than a cure.
Hackers stealing your customers’ credit card information is bad enough, but it’s not the worst. Clever hackers could also take control of your Web site or servers and use them to sell illegal merchandise or mount attacks on other sites. Shebby hasn’t heard of Web merchants being sued or prosecuted for not ensuring their sites are secure, but believes it is the direction things are headed.
How Hackers Wreak Havoc
Most use the same forms on the same Web pages where legitimate customers input their information, but hackers input special combinations of characters that can give them access to the database behind the application — with its trove of personal customer information — or let them take control of a site as if they were the owner.
The shopping cart software Smith used was vulnerable to two hacking techniques that he says were unheard of five years ago when the original cart software was developed. Since then, they’ve become so widespread, that it’s easy to find instructions on how to use them by Googling their names — SQL injection and cross-site scripting.
In SQL injection hacking, the perpetrator goes to a merchant site and inputs special character sequences in the User Name and Password fields. A vulnerable SQL-based application on the server interprets them (correctly) as commands rather than simple data input. One character string, for example, tells the software to accept as valid all user names and passwords entered from that point on.
|
|
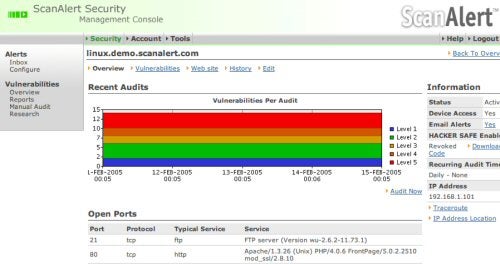
Mission Control — ScanAlert’s software reports on all vulnerabilities found on the site and displays the results over a five-day period. |
“I have to admit, it’s very, very clever,” Smith says. “It’s pretty easy to fix if you know about it, but you have to know about it.”
Cross-site scripting attacks vulnerabilities at sites where the data entry page posts customers’ input to a second page before completing the transaction. The site may be secure enough that the second page will not accept application commands from the first. But hackers have found ways to create their own bogus first pages, which then allow them to send commands to the application via the second page.
These are just two of thousands of vulnerabilities for which ScanAlert monitors, Shebby says. Some are application specific, others are more generic and can be found even in internally developed Web applications. Some are widely used by hackers, others are very rare. ScanAlert tests every site for all of them.
It uses automated systems to scan subscribers’ Web sites every day. Daily scanning is essential, the company says, because many Web sites change on an almost daily basis — and any change could expose an existing vulnerability. Hackers are also uncovering and exploiting entirely new vulnerabilities all the time. As soon as the company learns of new ones, it adds them to its scanning software.
“Our scans are perfectly safe,” Shebby adds. “We scan thousands of Web sites a day and we have no problems with servers not being able to handle them. It’s a very stable technology. It’s also very low noise — it never overloads the server.”
A Sign of Security
The ScanAlert service is mainly intended as a preventative, but the certification process brings additional benefits. The company says Hacker Safe certification signifies a Web site has “reduced its vulnerability to hackers by 99.99 percent by meeting the highest government and industry security standards.” ScanAlert tests to its own standards — which Shebby claims are the most stringent in the market — and also to Visa, MasterCard and FBI standards.
The company claims research shows that the presence of its Hacker Safe certification mark can also increase sales at a Web site. In one 2002 study conducted with 25,000 Internet shoppers at Binoculars.com, 50 percent of visitors saw the certification mark while the other 50 percent did not. The results showed 32 percent more shoppers purchased after seeing the certification mark.
Certainly online consumers are growing more concerned about the security risks involved in shopping on the Web. In an annual survey conducted by the TRUSTe organization — which is now partnering with ScanAlert to offer privacy and security certification — 44 percent of participants cited fear of credit card theft as a concern about online shipping. This is up from 30 percent in 2003.
Smith’s client opted to take the ScanAlert service for only one month to ensure the shopping cart software upgrade eliminated the vulnerabilities that had allowed hackers to get in the first place. Smith, who says he won’t be satisfied until the site goes six months without further incident, has urged the client to subscribe for a year, arguing that it would restore trust among customers affected by the earlier incidents.
“To me it’s the responsible thing to do,” he says. “But the clients I deal with are mostly very small — $2,000 is a lot of money to them. They’re more apt to say, ‘Let’s just wait and see what happens.'”
Which could be a big, big mistake.
Based in London, Canada, Gerry Blackwell has been writing about information technology and telecommunications for a variety of print and online publications since the 1980s. Just for fun, he also authors features and columns on digital photography for Here’s How, a spiffy new Canadian consumer technology magazine.
| Do you have a comment or question about this article or other small business topics in general? Speak out in the SmallBusinessComputing.com Forums. Join the discussion today! |

